Introduction
This blog post outlines the findings I came across of when analysing different types of data obfuscation found
in malicious RTF files. The research included performing static and dynamic analysis of publicly available
samples used for delivering the commodity malware. The main goal was to understand how native RTF parser is
treating unexpected data in control word groups, such as 'objdata'.
Executive Summary
Information in this blog post is intended for cybersecurity researchers and specialists developing RTF file
parsers. The research is based on the work already performed by other cybersecurity researchers and firms.
Its goal is to put some additional content on their work to enable the audience not so much familiar with
this area to better understand it.
As a part of this research, over 2000 experiments were performed. Each experiment aimed at establishing Microsoft native RTF
parser behavior when processing unexpected data. Knowing this behavior allows for reconstruction of the data
otherwise obfuscated for the purpose of hiding the malicious content and impeding the static signature based
detection.
Analysis
Disclaimer: The results observed might be specific to the test environment used. The same results can be
achieved by using other open/close source tools.
Obfuscation / Obfuscation Types
RTF files allow for a broad range of data obfuscation techniques. FireEye Threat Research group and Kaspersky
Labs explained most common techniques in their blog posts here
and here.
Where almost all of the techniques highlighted in the reports are still being used by the threat actors, there
were a few additions in the last 2.5 years. See the carousel below for some of the most common obfuscation types:
The techniques shown above can be found in the following malware samples:
Having such a variety of obfuscation techniques, makes it difficult to perform static analysis of the files
generated using those techniques. To be able to manually reconstruct the obfuscated objects, one would require to
know how RTF reader 'state machine' (Rich
Text Format (RTF) Specification, Version 1.9.1 (page 212)) will interpreter the data it reads.
The most trickiest part is the destination control word - '\*'. According to RTF Specification
Document, it serves the following purpose - 'Marks a destination whose text should be ignored if not
understood by the RTF reader.' It would be great if it was just that, but apparently its behavior
is a bit trickier due to the way it affects RTF reader internal state. Here is another comment on this
control
word from the specification document advising on things to consider when building an RTF parser.
Always understand \*
One of the most important things an RTF reader can do is to understand the \* control. This control introduces a destination that is not part of the document. It tells the RTF reader that if the reader does not understand the next control word, then it should skip the entire enclosing group.
Somewhat straight forward, but what happens when the RTF reader DOES understand the control word? How the RTF
reader state is going to be affected by the data contained in the destination group?
This blog post will attempt to shed some light on this very subject. The goal of my research was to establish the
Microsoft native RTF parser behavior when it encounters 'extra' groups or control words in 'objdata'
groups. Having done some OSINT research, I came to understanding that it's difficult to identify with 100%
certainty how a given unexpected data will be processed. It all boils down to the RTF control words and their
ability to consume (or not) the data right after them.
According to RTF specification document, there are 1814 control words. They are split into following 5
groups:
- Destinations
- Flags
- Symbols
- Toggles
- Values
Most commonly used in the 'objdata' group obfuscation are: destinations, symbols and flags. What adds
an extra bit of complexity is the '\*' control word. As will be shown later, the control words data
consumption behavior is different whether it's used inside a destination group or not.
The approach I've taken to identify the control words behavior is quite simple. I took all the destination and
flags control words and generated simple RTF files with them being inside a destination group and not. See below
for an example:
All in all, I ended up with 2358 RTF files. Fair question raises, how on Earth you're going to analyse 2358
files? On Earth, the answer is really simple - manually opening each one of them and witnessing the result with
your own eyes.
No matter how sad of a person some people might think I am after opening 2358 RTF files with Microsoft Office
Word, I recorded the results and built a searchable table (see Appendix section) to help me find a control word
behavior depending on its group location. Click on the 'Show' button below to see an example of a
search:
Consumes data means that any data following the control word will be consumed by
it and will NOT be present in the final 'objdata' group data. Following the example of a control word
given above, see how it affects the 'objdata' group data below:
{\*\objdata 010500000200000008000000{\*\mmaxdist 5061636b616765000} 000000000}
⇓
{\*\objdata 010500000200000008000000000000000}
{\*\objdata 010500000200000008000000{\mmaxdist 5061636b616765000}
000000000}
⇓
{\*\objdata 0105000002000000080000005061636b616765000000000000}
The table might come handy when building RTF parsing tools or peeling off some simple obfuscation, but when
things become a bit complicated we need a better approach. The section below describes a method that proved to
work with any obfuscation types.
The Silver Bullet
NOTE: It is strongly recommended that the following procedures to be
performed in an environment you may allow to be compromised.
FireEye report mentioned previously discusses a 'silver bullet' approach to
deobfuscating OLE objects embedded in RTF files. The gist of it is to intercept the call to
'OleConvertOLESTREAMToIStorage' function. The interception will allow to extract the reconstructed OLE
object before it's passed for further processing. The object will be fully deobfuscated as per Microsoft's
native RTF parser logic.
The section below is a walk-through for this method using x32dbg.
Should you be manually analysing an obfuscated RTF file or building an automation tools, the procedure below
might come helpful.
Test Environment
The following test environment was used:
- Virtualization: Virtual Box (5.2.10)
- Guest OS: Windows 7 Professional SP1
- Host Application: Microsoft Office 2007 (12.0.4518.1014)
- Debugger: x32dbg (build Aug 12 2018, 23:03:57)
- Text Editor: Notepad++ (v7.5.9 64-bit)
Pre-debugging Steps
Before opening a test RTF sample in Microsoft Word, the following steps must be completed:
- start Microsoft Word application
- start x32dbg application
- in x32dbg, go File -> Attach
- in the 'Attach' window, select 'WINWORD'
- click Attach button
- press F9 or click Run button in the top tool bar
Click 'Show' button below to see steps 3 - 6.
Debugging
NOTE: The following steps are based on this sample bcde46711f4b7c1b7cc0b2e490748472c04fdc74
Fair amount of obfuscation techniques is used in this test sample. It'll be rather challenging to reconstruct
the embedded OLE object manually. Before opening the sample with Microsoft Word, we need to setup a
breakpoint on 'OleConvertOLESTREAMToIStorage' function call. The steps below describe one way of doing
it:
- in x32dbg, go to Symbols tab
- click anywhere in the left pane and start typing ole32.dll
- click anywhere in the right pane and start typing OleConvertOLESTREAMToIStorage
- once the view is filtered, find reference to OleConvertOLESTREAMToIStorage and click on it
- press F2 or right click on it and select Toggle Breakpoint
- switch to Breakpoints tab and make sure there is an entry for OleConvertOLESTREAMToIStorage function call
Click 'Show' button below to see steps in action.
Now we're ready to open the test sample with Microsoft Word application and intercept the call to
'OleConvertOLESTREAMToIStorage' function. This will allow us to extract the embedded OLE object
directly from the memory after it was assembled by Microsoft's native RTF parser. Follow the steps below:
- in Microsoft Word, click on Office Button and select Open
- navigate to the location where the sample is stored
- double-click on the file or select the file and click Open button
- switch to x32dbg
At this stage we have loaded test sample into Microsoft Word and stopped its execution at
'OleConvertOLESTREAMToIStorage' function call. Our next step will be finding the assembled OLE object
in the memory. Follow the steps below:
- in x32dbg, right-click on the second line from the top in the stack pane
- select Follow DWORD in Dump
- select the DWORD value(4 bytes) in the third column of the first line in Dump 1 tab
- right-click the selected value and expand Follow DWORD in Dump menu
- select Dump 2 option
- select the DWORD value(4 bytes) in the first column of the first line in Dump 2 tab
- right-click the selected value and click Follow DWORD in Current Dump option
Dump 2 tab is now showing the embedded OLE object in the memory after it has been parsed by the native RTF
parser. It's now fully assembled and all the data obfuscation is removed. Before we can extract the object
from the memory, we need to take a note of the memory address where it's located and its length.
The address is currently being shown on the first line in Dump 2 tab. The length value is located next to
the value we selected first in Dump 1 tab. Switch to 'Dump 1' tab and take a note of the value
in the fourth column of the first line. Our next step is to carve it out of the memory and save it to the disk.
Follow the steps below to do so:
- click on Command text entry field (located at the bottom of x32dbg window)
- type savedata :memdump:, mem_addr, length
- press Enter key
The OLE object is now saved in X64DBG_INSTALL_PATH\release\x32\memdumps folder.
Click 'Show' button below to see all those steps in action.
If RTF file contains multiple embedded OLE objects, pressing F9 will continue the Microsoft Word execution
until the next OLE object is passed to 'OleConvertOLESTREAMToIStorage' function. At this point tough,
there is no guarantee your test machine will not be infected. Proceed with caution!
Aftermath
In this section we will review the results using some of the data obfuscation examples found in the original RTF
sample file. If you wish to follow along, open it in a text editor. I'll be using 'Notepad++' and
referencing pieces of data by their line positions in the file. You will also need a hex viewer/editor of your
choice.
First, let's describe the 'objdata' group that starts on line 67.
There are 2 groups that follow it right after its declaration - line 71. Each group contains 3 control words
followed by a piece of data.
Sequence of \' special characters begins on line 77. Their general purpose is to represent a HEX
value, based on the specified character set, but as can be seen in the given examples, the 'HEX'
characters do not conform to hex value representation format.
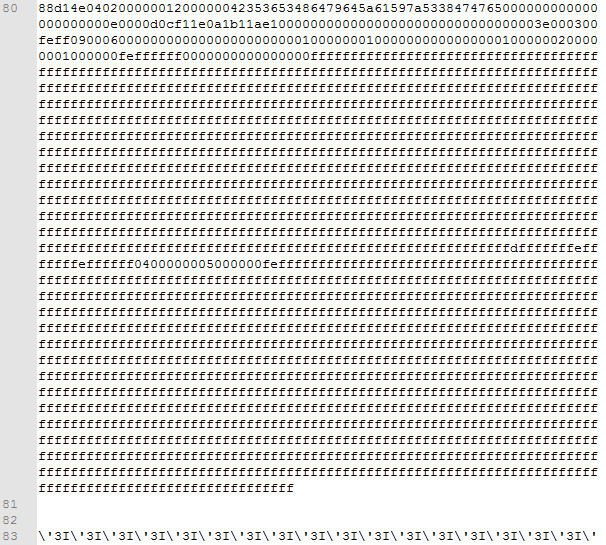
Plain text data begins on line 80 and followed by another special characters obfuscation starting on line 83.
Interesting group at line 95 contains a non-printable character followed by a hex string. This group also
preceded by destination control word - '\*'.
Another group (line 100) containing 2 control words.
Sequence of escaped expressions begins at line 103.
The last interesting piece for us is on line 111 - \bin control word is used to convert 'P'
character into a hex value.
Now open the OLE object carved from the memory in a hex viewer/editor. The carved object begins with the
following bytes: 88 D1 4E 04 02 00 00 00. The same sequence can be found in the original RTF sample file
starting at line 80. This means that all the data from the beginning of 'objdata' group (line 67) up to
line 80 has been discarded. This includes the 2 groups and the sequence of \' special characters we
noted earlier.
The data from the interesting group at line 95 does not appear to be present in the carved OLE object. We can
easily locate the data preceding it - 00 6F 00 74 00 20 00 45 00 6E 00 74 00 72 00 (offset 0x42D), but
not the data from the group. Byte 79(offset 0x43C) follows the preceding data, meaning the interesting
group data has been discarded.
As expected the data from the group at line 100 has been discarded, but the sequence of escaped expressions
appear to be present in the carved OLE object. It begins at offset 0x43D and ends at 0x829.
The last piece of data we're interested in is the one supplied to \bin control word. It's only 1
byte long and it's represented by 'P' character in the original RTF sample. We would expect it to
follow the sequence of escaped expressions and the plain text string - 700 located at line 108.
Character P has a hex value of 50. Our expected byte sequence is 70 05 00 00 02 D3, but
interestingly enough, there isn't such byte sequence present in the carved OLE object. Something isn't
the way we expected it to be after analysing the original RTF file manually. According to the native RTF parser,
this data transforms into this byte sequence - 70 50 00 00 02 D3.
Couple of things to note here:
- the last 0 in 700 string disappears
- the number of zeros after 50 (P converted to hex) is 5 and not expected 4
The last example shows how unexpected the results can be when trying to deobfuscate RTF embedded OLE objects
manually. Where doing it this way is fun and challenging, the only way to make sure the deobfuscation has been
successful is to compare it with the results of Microsoft's native RTF parser.
Credits
Huge shout out to Andrew Torres for crash course on Microsoft
Office applications debugging with x32dbg and overall feedback. This dude is a wizard!
Kudos to Decalage and Didier
Stevens for peer reviewing the wall of text above. I really appreciate it, folks!
External References
Appendix
Control Words Search Table
| Control Word | Destination Flag (FALSE) | Destination Flag (TRUE) |
|---|---|---|
| ApplyBrkRules | Does not consume data | Does not consume data |
| abslock | Does not consume data | Does not consume data |
| additive | Does not consume data | Does not consume data |
| adjustright | Does not consume data | Does not consume data |
| aenddoc | Does not consume data | Does not consume data |
| aendnotes | Does not consume data | Does not consume data |
| afelev | Does not consume data | Does not consume data |
| aftnbj | Does not consume data | Does not consume data |
| aftncn | Consumes data | Consumes data |
| aftnnalc | Does not consume data | Does not consume data |
| aftnnar | Does not consume data | Does not consume data |
| aftnnauc | Does not consume data | Does not consume data |
| aftnnchi | Does not consume data | Does not consume data |
| aftnnchosung | Does not consume data | Does not consume data |
| aftnncnum | Does not consume data | Does not consume data |
| aftnndbar | Does not consume data | Does not consume data |
| aftnndbnum | Does not consume data | Does not consume data |
| aftnndbnumd | Does not consume data | Does not consume data |
| aftnndbnumk | Does not consume data | Does not consume data |
| aftnndbnumt | Does not consume data | Does not consume data |
| aftnnganada | Does not consume data | Does not consume data |
| aftnngbnum | Does not consume data | Does not consume data |
| aftnngbnumd | Does not consume data | Does not consume data |
| aftnngbnumk | Does not consume data | Does not consume data |
| aftnngbnuml | Does not consume data | Does not consume data |
| aftnnrlc | Does not consume data | Does not consume data |
| aftnnruc | Does not consume data | Does not consume data |
| aftnnzodiac | Does not consume data | Does not consume data |
| aftnnzodiacd | Does not consume data | Does not consume data |
| aftnnzodiacl | Does not consume data | Does not consume data |
| aftnrestart | Does not consume data | Does not consume data |
| aftnrstcont | Does not consume data | Does not consume data |
| aftnsep | Consumes data | Consumes data |
| aftnsepc | Consumes data | Consumes data |
| aftntj | Does not consume data | Does not consume data |
| allowfieldendsel | Does not consume data | Does not consume data |
| allprot | Does not consume data | Does not consume data |
| alntblind | Does not consume data | Does not consume data |
| alt | Does not consume data | Consumes data |
| annotation | Consumes data | Consumes data |
| annotprot | Does not consume data | Does not consume data |
| ansi | Does not consume data | Does not consume data |
| asianbrkrule | Does not consume data | Does not consume data |
| atnauthor | Consumes data | Consumes data |
| atndate | Consumes data | Consumes data |
| atnicn | Does not consume data | Consumes data |
| atnid | Consumes data | Consumes data |
| atnparent | Consumes data | Consumes data |
| atnref | Consumes data | Consumes data |
| atntime | Does not consume data | Consumes data |
| atrfend | Consumes data | Consumes data |
| atrfstart | Consumes data | Consumes data |
| author | Consumes data | Consumes data |
| autofmtoverride | Does not consume data | Does not consume data |
| background | Consumes data | Consumes data |
| bdbfhdr | Does not consume data | Does not consume data |
| bdrrlswsix | Does not consume data | Does not consume data |
| bgbdiag | Does not consume data | Does not consume data |
| bgcross | Does not consume data | Does not consume data |
| bgdcross | Does not consume data | Does not consume data |
| bgdkbdiag | Does not consume data | Does not consume data |
| bgdkcross | Does not consume data | Does not consume data |
| bgdkdcross | Does not consume data | Does not consume data |
| bgdkfdiag | Does not consume data | Does not consume data |
| bgdkhoriz | Does not consume data | Does not consume data |
| bgdkvert | Does not consume data | Does not consume data |
| bgfdiag | Does not consume data | Does not consume data |
| bghoriz | Does not consume data | Does not consume data |
| bgvert | Does not consume data | Does not consume data |
| bkmkend | Consumes data | Consumes data |
| bkmkpub | Does not consume data | Does not consume data |
| bkmkstart | Consumes data | Consumes data |
| blipuid | Consumes data | Consumes data |
| bookfold | Does not consume data | Does not consume data |
| bookfoldrev | Does not consume data | Does not consume data |
| box | Does not consume data | Does not consume data |
| brdrb | Does not consume data | Does not consume data |
| brdrbar | Does not consume data | Does not consume data |
| brdrbtw | Does not consume data | Does not consume data |
| brdrdash | Does not consume data | Does not consume data |
| brdrdashd | Does not consume data | Does not consume data |
| brdrdashdd | Does not consume data | Does not consume data |
| brdrdashdot | Does not consume data | Does not consume data |
| brdrdashdotdot | Does not consume data | Does not consume data |
| brdrdashdotstr | Does not consume data | Does not consume data |
| brdrdashsm | Does not consume data | Does not consume data |
| brdrdb | Does not consume data | Does not consume data |
| brdrdot | Does not consume data | Does not consume data |
| brdremboss | Does not consume data | Does not consume data |
| brdrengrave | Does not consume data | Does not consume data |
| brdrframe | Does not consume data | Does not consume data |
| brdrhair | Does not consume data | Does not consume data |
| brdrinset | Does not consume data | Does not consume data |
| brdrl | Does not consume data | Does not consume data |
| brdrnil | Does not consume data | Does not consume data |
| brdrnone | Does not consume data | Does not consume data |
| brdroutset | Does not consume data | Does not consume data |
| brdrr | Does not consume data | Does not consume data |
| brdrs | Does not consume data | Does not consume data |
| brdrsh | Does not consume data | Does not consume data |
| brdrt | Does not consume data | Does not consume data |
| brdrtbl | Does not consume data | Does not consume data |
| brdrth | Does not consume data | Does not consume data |
| brdrthtnlg | Does not consume data | Does not consume data |
| brdrthtnmg | Does not consume data | Does not consume data |
| brdrthtnsg | Does not consume data | Does not consume data |
| brdrtnthlg | Does not consume data | Does not consume data |
| brdrtnthmg | Does not consume data | Does not consume data |
| brdrtnthsg | Does not consume data | Does not consume data |
| brdrtnthtnlg | Does not consume data | Does not consume data |
| brdrtnthtnmg | Does not consume data | Does not consume data |
| brdrtnthtnsg | Does not consume data | Does not consume data |
| brdrtriple | Does not consume data | Does not consume data |
| brdrwavy | Does not consume data | Does not consume data |
| brdrwavydb | Does not consume data | Does not consume data |
| brkfrm | Does not consume data | Does not consume data |
| buptim | Consumes data | Consumes data |
| bxe | Does not consume data | Does not consume data |
| caccentfive | Does not consume data | Does not consume data |
| caccentfour | Does not consume data | Does not consume data |
| caccentone | Does not consume data | Does not consume data |
| caccentsix | Does not consume data | Does not consume data |
| caccentthree | Does not consume data | Does not consume data |
| caccenttwo | Does not consume data | Does not consume data |
| cachedcolbal | Does not consume data | Does not consume data |
| category | Consumes data | Consumes data |
| cbackgroundone | Does not consume data | Does not consume data |
| cbackgroundtwo | Does not consume data | Does not consume data |
| cfollowedhyperlink | Does not consume data | Does not consume data |
| chbgbdiag | Does not consume data | Does not consume data |
| chbgcross | Does not consume data | Does not consume data |
| chbgdcross | Does not consume data | Does not consume data |
| chbgdkbdiag | Does not consume data | Does not consume data |
| chbgdkcross | Does not consume data | Does not consume data |
| chbgdkdcross | Does not consume data | Does not consume data |
| chbgdkfdiag | Does not consume data | Does not consume data |
| chbgdkhoriz | Does not consume data | Does not consume data |
| chbgdkvert | Does not consume data | Does not consume data |
| chbgfdiag | Does not consume data | Does not consume data |
| chbghoriz | Does not consume data | Does not consume data |
| chbgvert | Does not consume data | Does not consume data |
| chbrdr | Does not consume data | Does not consume data |
| chyperlink | Does not consume data | Does not consume data |
| clFitText | Does not consume data | Does not consume data |
| clNoWrap | Does not consume data | Does not consume data |
| clbgbdiag | Does not consume data | Does not consume data |
| clbgcross | Does not consume data | Does not consume data |
| clbgdcross | Does not consume data | Does not consume data |
| clbgdkbdiag | Does not consume data | Does not consume data |
| clbgdkcross | Does not consume data | Does not consume data |
| clbgdkdcross | Does not consume data | Does not consume data |
| clbgdkfdiag | Does not consume data | Does not consume data |
| clbgdkhor | Does not consume data | Does not consume data |
| clbgdkvert | Does not consume data | Does not consume data |
| clbgfdiag | Does not consume data | Does not consume data |
| clbghoriz | Does not consume data | Does not consume data |
| clbgvert | Does not consume data | Does not consume data |
| clbrdrb | Does not consume data | Does not consume data |
| clbrdrl | Does not consume data | Does not consume data |
| clbrdrr | Does not consume data | Does not consume data |
| clbrdrt | Does not consume data | Does not consume data |
| cldel | Does not consume data | Does not consume data |
| cldgll | Does not consume data | Does not consume data |
| cldglu | Does not consume data | Does not consume data |
| clhidemark | Does not consume data | Does not consume data |
| clins | Does not consume data | Does not consume data |
| clmgf | Does not consume data | Does not consume data |
| clmrg | Does not consume data | Does not consume data |
| clmrgd | Does not consume data | Does not consume data |
| clmrgdr | Does not consume data | Does not consume data |
| clshdrawnil | Does not consume data | Does not consume data |
| clsplit | Does not consume data | Does not consume data |
| clsplitr | Does not consume data | Does not consume data |
| cltxbtlr | Does not consume data | Does not consume data |
| cltxlrtb | Does not consume data | Does not consume data |
| cltxlrtbv | Does not consume data | Does not consume data |
| cltxtbrl | Does not consume data | Does not consume data |
| cltxtbrlv | Does not consume data | Does not consume data |
| clvertalb | Does not consume data | Does not consume data |
| clvertalc | Does not consume data | Does not consume data |
| clvertalt | Does not consume data | Does not consume data |
| clvmgf | Does not consume data | Does not consume data |
| clvmrg | Does not consume data | Does not consume data |
| cmaindarkone | Does not consume data | Does not consume data |
| cmaindarktwo | Does not consume data | Does not consume data |
| cmainlightone | Does not consume data | Does not consume data |
| cmainlighttwo | Does not consume data | Does not consume data |
| collapsed | Does not consume data | Consumes data |
| colorschememapping | Consumes data | Consumes data |
| colortbl | Consumes data | Consumes data |
| comment | Consumes data | Consumes data |
| company | Consumes data | Consumes data |
| contextualspace | Does not consume data | Does not consume data |
| creatim | Consumes data | Consumes data |
| ctextone | Does not consume data | Does not consume data |
| ctexttwo | Does not consume data | Does not consume data |
| ctrl | Does not consume data | Does not consume data |
| cvmme | Does not consume data | Does not consume data |
| datafield | Consumes data | Consumes data |
| datastore | Consumes data | Consumes data |
| date | Does not consume data | Does not consume data |
| dbch | Does not consume data | Does not consume data |
| defchp | Consumes data | Consumes data |
| defformat | Does not consume data | Does not consume data |
| defpap | Consumes data | Consumes data |
| defshp | Does not consume data | Does not consume data |
| dgmargin | Does not consume data | Does not consume data |
| dgsnap | Does not consume data | Consumes data |
| dntblnsbdb | Does not consume data | Does not consume data |
| do | Consumes data | Consumes data |
| dobxcolumn | Does not consume data | Does not consume data |
| dobxmargin | Does not consume data | Does not consume data |
| dobxpage | Does not consume data | Does not consume data |
| dobymargin | Does not consume data | Does not consume data |
| dobypage | Does not consume data | Does not consume data |
| dobypara | Does not consume data | Does not consume data |
| doccomm | Consumes data | Consumes data |
| doctemp | Does not consume data | Consumes data |
| docvar | Consumes data | Consumes data |
| dolock | Does not consume data | Does not consume data |
| donotshowcomments | Does not consume data | Does not consume data |
| donotshowinsdel | Does not consume data | Does not consume data |
| donotshowmarkup | Does not consume data | Does not consume data |
| donotshowprops | Does not consume data | Does not consume data |
| dpaendhol | Does not consume data | Does not consume data |
| dpaendsol | Does not consume data | Does not consume data |
| dparc | Does not consume data | Does not consume data |
| dparcflipx | Does not consume data | Does not consume data |
| dparcflipy | Does not consume data | Does not consume data |
| dpastarthol | Does not consume data | Does not consume data |
| dpastartsol | Does not consume data | Does not consume data |
| dpcallout | Does not consume data | Does not consume data |
| dpcoaccent | Does not consume data | Does not consume data |
| dpcobestfit | Does not consume data | Does not consume data |
| dpcoborder | Does not consume data | Does not consume data |
| dpcodabs | Does not consume data | Does not consume data |
| dpcodbottom | Does not consume data | Does not consume data |
| dpcodcenter | Does not consume data | Does not consume data |
| dpcodtop | Does not consume data | Does not consume data |
| dpcominusx | Does not consume data | Does not consume data |
| dpcominusy | Does not consume data | Does not consume data |
| dpcosmarta | Does not consume data | Does not consume data |
| dpcotdouble | Does not consume data | Does not consume data |
| dpcotright | Does not consume data | Does not consume data |
| dpcotsingle | Does not consume data | Does not consume data |
| dpcottriple | Does not consume data | Does not consume data |
| dpellipse | Does not consume data | Does not consume data |
| dpendgroup | Does not consume data | Does not consume data |
| dpfillbgpal | Does not consume data | Does not consume data |
| dpfillfgpal | Does not consume data | Does not consume data |
| dpgroup | Does not consume data | Does not consume data |
| dpline | Does not consume data | Does not consume data |
| dplinedado | Does not consume data | Does not consume data |
| dplinedadodo | Does not consume data | Does not consume data |
| dplinedash | Does not consume data | Does not consume data |
| dplinedot | Does not consume data | Does not consume data |
| dplinehollow | Does not consume data | Does not consume data |
| dplinepal | Does not consume data | Does not consume data |
| dplinesolid | Does not consume data | Does not consume data |
| dppolygon | Does not consume data | Does not consume data |
| dppolyline | Does not consume data | Does not consume data |
| dprect | Does not consume data | Does not consume data |
| dproundr | Does not consume data | Does not consume data |
| dpshadow | Does not consume data | Does not consume data |
| dptxbtlr | Does not consume data | Does not consume data |
| dptxbx | Does not consume data | Does not consume data |
| dptxbxtext | Consumes data | Consumes data |
| dptxlrtb | Does not consume data | Does not consume data |
| dptxlrtbv | Does not consume data | Does not consume data |
| dptxtbrl | Does not consume data | Does not consume data |
| dptxtbrlv | Does not consume data | Does not consume data |
| ebcend | Consumes data | Consumes data |
| ebcstart | Consumes data | Consumes data |
| emfblip | Does not consume data | Does not consume data |
| enddoc | Does not consume data | Does not consume data |
| endnhere | Does not consume data | Does not consume data |
| endnotes | Does not consume data | Does not consume data |
| expshrtn | Does not consume data | Does not consume data |
| faauto | Does not consume data | Does not consume data |
| facenter | Does not consume data | Does not consume data |
| facingp | Does not consume data | Does not consume data |
| factoidname | Consumes data | Consumes data |
| fafixed | Does not consume data | Consumes data |
| fahang | Does not consume data | Does not consume data |
| falt | Consumes data | Consumes data |
| faroman | Does not consume data | Does not consume data |
| favar | Does not consume data | Does not consume data |
| fbidi | Does not consume data | Does not consume data |
| fbidis | Does not consume data | Does not consume data |
| fbimajor | Does not consume data | Does not consume data |
| fbiminor | Does not consume data | Does not consume data |
| fchars | Consumes data | Consumes data |
| fdbmajor | Does not consume data | Does not consume data |
| fdbminor | Does not consume data | Does not consume data |
| fdecor | Does not consume data | Does not consume data |
| felnbrelev | Does not consume data | Does not consume data |
| fetch | Does not consume data | Consumes data |
| ffdeftext | Consumes data | Consumes data |
| ffentrymcr | Consumes data | Consumes data |
| ffexitmcr | Consumes data | Consumes data |
| ffformat | Consumes data | Consumes data |
| ffhelptext | Consumes data | Consumes data |
| ffl | Consumes data | Consumes data |
| ffname | Consumes data | Consumes data |
| ffstattext | Consumes data | Consumes data |
| fhimajor | Does not consume data | Does not consume data |
| fhiminor | Does not consume data | Does not consume data |
| field | Consumes data | Consumes data |
| file | Consumes data | Consumes data |
| filetbl | Consumes data | Consumes data |
| fjgothic | Does not consume data | Consumes data |
| fjminchou | Does not consume data | Consumes data |
| fldalt | Does not consume data | Does not consume data |
| flddirty | Does not consume data | Does not consume data |
| fldedit | Does not consume data | Does not consume data |
| fldinst | Consumes data | Consumes data |
| fldlock | Does not consume data | Does not consume data |
| fldpriv | Does not consume data | Does not consume data |
| fldrslt | Consumes data | Consumes data |
| fldtype | Consumes data | Consumes data |
| flomajor | Does not consume data | Does not consume data |
| flominor | Does not consume data | Does not consume data |
| fmodern | Does not consume data | Does not consume data |
| fname | Does not consume data | Consumes data |
| fnetwork | Does not consume data | Does not consume data |
| fnil | Does not consume data | Does not consume data |
| fnonfilesys | Does not consume data | Does not consume data |
| fontemb | Consumes data | Consumes data |
| fontfile | Does not consume data | Consumes data |
| fonttbl | Consumes data | Consumes data |
| footer | Consumes data | Consumes data |
| footerf | Consumes data | Consumes data |
| footerl | Consumes data | Consumes data |
| footerr | Consumes data | Consumes data |
| footnote | Consumes data | Consumes data |
| forceupgrade | Does not consume data | Does not consume data |
| formdisp | Does not consume data | Does not consume data |
| formfield | Consumes data | Consumes data |
| formprot | Does not consume data | Does not consume data |
| formshade | Does not consume data | Does not consume data |
| fracwidth | Does not consume data | Does not consume data |
| frmtxbtlr | Does not consume data | Does not consume data |
| frmtxlrtb | Does not consume data | Does not consume data |
| frmtxlrtbv | Does not consume data | Does not consume data |
| frmtxtbrl | Does not consume data | Does not consume data |
| frmtxtbrlv | Does not consume data | Does not consume data |
| froman | Does not consume data | Does not consume data |
| fromtext | Does not consume data | Does not consume data |
| fscript | Does not consume data | Does not consume data |
| fswiss | Does not consume data | Does not consume data |
| ftech | Does not consume data | Does not consume data |
| ftfalsetype | Does not consume data | Consumes data |
| ftnalt | Does not consume data | Does not consume data |
| ftnbj | Does not consume data | Does not consume data |
| ftncn | Consumes data | Consumes data |
| ftnil | Does not consume data | Does not consume data |
| ftnlytwnine | Does not consume data | Does not consume data |
| ftnnalc | Does not consume data | Does not consume data |
| ftnnar | Does not consume data | Does not consume data |
| ftnnauc | Does not consume data | Does not consume data |
| ftnnchi | Does not consume data | Does not consume data |
| ftnnchosung | Does not consume data | Does not consume data |
| ftnncnum | Does not consume data | Does not consume data |
| ftnndbar | Does not consume data | Does not consume data |
| ftnndbnum | Does not consume data | Does not consume data |
| ftnndbnumd | Does not consume data | Does not consume data |
| ftnndbnumk | Does not consume data | Does not consume data |
| ftnndbnumt | Does not consume data | Does not consume data |
| ftnnganada | Does not consume data | Does not consume data |
| ftnngbnum | Does not consume data | Does not consume data |
| ftnngbnumd | Does not consume data | Does not consume data |
| ftnngbnumk | Does not consume data | Does not consume data |
| ftnngbnuml | Does not consume data | Does not consume data |
| ftnnrlc | Does not consume data | Does not consume data |
| ftnnruc | Does not consume data | Does not consume data |
| ftnnzodiac | Does not consume data | Does not consume data |
| ftnnzodiacd | Does not consume data | Does not consume data |
| ftnnzodiacl | Does not consume data | Does not consume data |
| ftnrestart | Does not consume data | Does not consume data |
| ftnrstcont | Does not consume data | Does not consume data |
| ftnrstpg | Does not consume data | Does not consume data |
| ftnsep | Consumes data | Consumes data |
| ftnsepc | Consumes data | Consumes data |
| ftntj | Does not consume data | Does not consume data |
| fvaliddos | Does not consume data | Does not consume data |
| fvalidhpfs | Does not consume data | Does not consume data |
| fvalidmac | Does not consume data | Does not consume data |
| fvalidntfs | Does not consume data | Does not consume data |
| g | Consumes data | Consumes data |
| generator | Consumes data | Consumes data |
| gridtbl | Consumes data | Consumes data |
| gutterprl | Does not consume data | Does not consume data |
| header | Consumes data | Consumes data |
| headerf | Consumes data | Consumes data |
| headerl | Consumes data | Consumes data |
| headerr | Consumes data | Consumes data |
| hich | Does not consume data | Does not consume data |
| hl | Consumes data | Consumes data |
| hlfr | Consumes data | Consumes data |
| hlinkbase | Consumes data | Consumes data |
| hlloc | Consumes data | Consumes data |
| hlsrc | Consumes data | Consumes data |
| horzdoc | Does not consume data | Does not consume data |
| horzsect | Does not consume data | Does not consume data |
| hrule | Consumes data | Consumes data |
| hsv | Consumes data | Consumes data |
| htmautsp | Does not consume data | Does not consume data |
| htmlbase | Does not consume data | Consumes data |
| htmltag | Does not consume data | Consumes data |
| hwelev | Does not consume data | Does not consume data |
| indmirror | Does not consume data | Does not consume data |
| indrlsweleven | Does not consume data | Does not consume data |
| info | Consumes data | Consumes data |
| intbl | Does not consume data | Does not consume data |
| ixe | Does not consume data | Does not consume data |
| jclisttab | Does not consume data | Does not consume data |
| jcompress | Does not consume data | Does not consume data |
| jexpand | Does not consume data | Does not consume data |
| jis | Does not consume data | Does not consume data |
| jpegblip | Does not consume data | Does not consume data |
| jsksu | Does not consume data | Does not consume data |
| keep | Does not consume data | Does not consume data |
| keepn | Does not consume data | Does not consume data |
| keycode | Does not consume data | Does not consume data |
| keywords | Consumes data | Consumes data |
| krnprsnet | Does not consume data | Does not consume data |
| landscape | Does not consume data | Does not consume data |
| lastrow | Does not consume data | Does not consume data |
| latentstyles | Consumes data | Consumes data |
| lchars | Consumes data | Consumes data |
| levelnumbers | Consumes data | Consumes data |
| levelpicturenosize | Does not consume data | Does not consume data |
| leveltext | Consumes data | Consumes data |
| lfolevel | Consumes data | Consumes data |
| linebetcol | Does not consume data | Does not consume data |
| linecont | Does not consume data | Does not consume data |
| lineppage | Does not consume data | Does not consume data |
| linerestart | Does not consume data | Does not consume data |
| linkself | Does not consume data | Consumes data |
| linkstyles | Does not consume data | Does not consume data |
| linkval | Consumes data | Consumes data |
| list | Consumes data | Consumes data |
| listhybrid | Does not consume data | Does not consume data |
| listlevel | Consumes data | Consumes data |
| listname | Consumes data | Consumes data |
| listoverride | Consumes data | Consumes data |
| listoverridestartat | Does not consume data | Does not consume data |
| listoverridetable | Consumes data | Consumes data |
| listpicture | Consumes data | Consumes data |
| liststylename | Consumes data | Consumes data |
| listtable | Consumes data | Consumes data |
| listtext | Consumes data | Consumes data |
| lnbrkrule | Does not consume data | Does not consume data |
| lndscpsxn | Does not consume data | Does not consume data |
| lnongrid | Does not consume data | Does not consume data |
| loch | Does not consume data | Does not consume data |
| lsdlockedexcept | Consumes data | Consumes data |
| ltrch | Does not consume data | Does not consume data |
| ltrdoc | Does not consume data | Does not consume data |
| ltrpar | Does not consume data | Does not consume data |
| ltrrow | Does not consume data | Does not consume data |
| ltrsect | Does not consume data | Does not consume data |
| lvltentative | Does not consume data | Does not consume data |
| lytcalctblwd | Does not consume data | Does not consume data |
| lytexcttp | Does not consume data | Does not consume data |
| lytprtmet | Does not consume data | Does not consume data |
| lyttblrtgr | Does not consume data | Does not consume data |
| mac | Does not consume data | Does not consume data |
| macc | Consumes data | Consumes data |
| maccPr | Consumes data | Consumes data |
| macpict | Does not consume data | Does not consume data |
| mailmerge | Consumes data | Consumes data |
| makebackup | Does not consume data | Does not consume data |
| maln | Does not consume data | Does not consume data |
| malnScr | Consumes data | Consumes data |
| manager | Consumes data | Consumes data |
| margPr | Consumes data | Consumes data |
| margmirror | Does not consume data | Does not consume data |
| margmirsxn | Does not consume data | Does not consume data |
| mbar | Consumes data | Consumes data |
| mbarPr | Consumes data | Consumes data |
| mbaseJc | Consumes data | Consumes data |
| mbegChr | Consumes data | Consumes data |
| mborderBox | Consumes data | Consumes data |
| mborderBoxPr | Consumes data | Consumes data |
| mbox | Consumes data | Consumes data |
| mboxPr | Consumes data | Consumes data |
| mchr | Consumes data | Consumes data |
| mcount | Consumes data | Consumes data |
| mctrlPr | Consumes data | Consumes data |
| md | Consumes data | Consumes data |
| mdPr | Consumes data | Consumes data |
| mdeg | Consumes data | Consumes data |
| mdegHide | Consumes data | Consumes data |
| mden | Consumes data | Consumes data |
| mdiff | Consumes data | Consumes data |
| me | Consumes data | Consumes data |
| mendChr | Consumes data | Consumes data |
| meqArr | Consumes data | Consumes data |
| meqArrPr | Consumes data | Consumes data |
| mf | Consumes data | Consumes data |
| mfName | Consumes data | Consumes data |
| mfPr | Consumes data | Consumes data |
| mfunc | Consumes data | Consumes data |
| mfuncPr | Consumes data | Consumes data |
| mgroupChr | Consumes data | Consumes data |
| mgroupChrPr | Consumes data | Consumes data |
| mgrow | Consumes data | Consumes data |
| mhideBot | Consumes data | Consumes data |
| mhideLeft | Consumes data | Consumes data |
| mhideRight | Consumes data | Consumes data |
| mhideTop | Consumes data | Consumes data |
| mhtmltag | Does not consume data | Consumes data |
| mlim | Consumes data | Consumes data |
| mlimLow | Consumes data | Consumes data |
| mlimloc | Does not consume data | Consumes data |
| mlimlow | Does not consume data | Consumes data |
| mlimlowPr | Does not consume data | Consumes data |
| mlimupp | Does not consume data | Consumes data |
| mlimuppPr | Does not consume data | Consumes data |
| mlit | Does not consume data | Does not consume data |
| mm | Consumes data | Consumes data |
| mmPr | Consumes data | Consumes data |
| mmaddfieldname | Consumes data | Consumes data |
| mmath | Does not consume data | Does not consume data |
| mmathPict | Consumes data | Consumes data |
| mmathPr | Does not consume data | Does not consume data |
| mmattach | Does not consume data | Does not consume data |
| mmaxdist | Does not consume data | Consumes data |
| mmblanklines | Does not consume data | Does not consume data |
| mmc | Consumes data | Consumes data |
| mmcJc | Consumes data | Consumes data |
| mmcPr | Consumes data | Consumes data |
| mmconnectstr | Consumes data | Consumes data |
| mmconnectstrdata | Consumes data | Consumes data |
| mmcs | Consumes data | Consumes data |
| mmdatasource | Consumes data | Consumes data |
| mmdatatypeaccess | Does not consume data | Does not consume data |
| mmdatatypeexcel | Does not consume data | Does not consume data |
| mmdatatypefile | Does not consume data | Does not consume data |
| mmdatatypeodbc | Does not consume data | Does not consume data |
| mmdatatypeodso | Does not consume data | Does not consume data |
| mmdatatypeqt | Does not consume data | Does not consume data |
| mmdefaultsql | Does not consume data | Does not consume data |
| mmdestemail | Does not consume data | Does not consume data |
| mmdestfax | Does not consume data | Does not consume data |
| mmdestnewdoc | Does not consume data | Does not consume data |
| mmdestprinter | Does not consume data | Does not consume data |
| mmfttypeaddress | Does not consume data | Does not consume data |
| mmfttypebarcode | Does not consume data | Does not consume data |
| mmfttypedbcolumn | Does not consume data | Does not consume data |
| mmfttypemapped | Does not consume data | Does not consume data |
| mmfttypenull | Does not consume data | Does not consume data |
| mmfttypesalutation | Does not consume data | Does not consume data |
| mmheadersource | Consumes data | Consumes data |
| mmlinktoquery | Does not consume data | Does not consume data |
| mmmailsubject | Consumes data | Consumes data |
| mmmaintypecatalog | Does not consume data | Does not consume data |
| mmmaintypeemail | Does not consume data | Does not consume data |
| mmmaintypeenvelopes | Does not consume data | Does not consume data |
| mmmaintypefax | Does not consume data | Does not consume data |
| mmmaintypelabels | Does not consume data | Does not consume data |
| mmmaintypeletters | Does not consume data | Does not consume data |
| mmodso | Consumes data | Consumes data |
| mmodsofilter | Consumes data | Consumes data |
| mmodsofldmpdata | Consumes data | Consumes data |
| mmodsomappedname | Consumes data | Consumes data |
| mmodsoname | Consumes data | Consumes data |
| mmodsorecipdata | Consumes data | Consumes data |
| mmodsosort | Consumes data | Consumes data |
| mmodsosrc | Consumes data | Consumes data |
| mmodsotable | Consumes data | Consumes data |
| mmodsoudl | Consumes data | Consumes data |
| mmodsoudldata | Consumes data | Consumes data |
| mmodsouniquetag | Consumes data | Consumes data |
| mmquery | Consumes data | Consumes data |
| mmr | Consumes data | Consumes data |
| mmshowdata | Does not consume data | Does not consume data |
| mnary | Consumes data | Consumes data |
| mnaryPr | Consumes data | Consumes data |
| mnoBreak | Consumes data | Consumes data |
| mnor | Does not consume data | Does not consume data |
| mnum | Consumes data | Consumes data |
| moMath | Consumes data | Consumes data |
| moMathPara | Consumes data | Consumes data |
| moMathParaPr | Consumes data | Consumes data |
| mobjDist | Consumes data | Consumes data |
| mopEmu | Consumes data | Consumes data |
| mphant | Consumes data | Consumes data |
| mphantPr | Consumes data | Consumes data |
| mplcHide | Consumes data | Consumes data |
| mpos | Consumes data | Consumes data |
| mr | Consumes data | Consumes data |
| mrPr | Consumes data | Consumes data |
| mrad | Consumes data | Consumes data |
| mradPr | Consumes data | Consumes data |
| msPre | Consumes data | Consumes data |
| msPrePr | Consumes data | Consumes data |
| msSub | Consumes data | Consumes data |
| msSubPr | Consumes data | Consumes data |
| msSubSup | Consumes data | Consumes data |
| msSubSupPr | Consumes data | Consumes data |
| msSup | Consumes data | Consumes data |
| msSupPr | Consumes data | Consumes data |
| msepChr | Consumes data | Consumes data |
| mshow | Consumes data | Consumes data |
| mshp | Consumes data | Consumes data |
| msmcap | Does not consume data | Does not consume data |
| mstrikeBLTR | Consumes data | Consumes data |
| mstrikeH | Consumes data | Consumes data |
| mstrikeTLBR | Consumes data | Consumes data |
| mstrikeV | Consumes data | Consumes data |
| msub | Consumes data | Consumes data |
| msubHide | Consumes data | Consumes data |
| msup | Consumes data | Consumes data |
| msupHide | Consumes data | Consumes data |
| mtransp | Consumes data | Consumes data |
| mtype | Consumes data | Consumes data |
| muser | Does not consume data | Does not consume data |
| mvertJc | Consumes data | Consumes data |
| mvf | Does not consume data | Does not consume data |
| mvfmf | Consumes data | Consumes data |
| mvfml | Consumes data | Consumes data |
| mvt | Does not consume data | Does not consume data |
| mvtof | Consumes data | Consumes data |
| mvtol | Consumes data | Consumes data |
| mzeroAsc | Consumes data | Consumes data |
| mzeroDesc | Consumes data | Consumes data |
| mzeroWid | Consumes data | Consumes data |
| nesttableprops | Consumes data | Consumes data |
| newtblstyruls | Does not consume data | Does not consume data |
| nextfile | Does not consume data | Consumes data |
| noafcnsttbl | Does not consume data | Does not consume data |
| nobrkwrptbl | Does not consume data | Does not consume data |
| nocolbal | Does not consume data | Does not consume data |
| nocompatoptions | Does not consume data | Does not consume data |
| nocwrap | Does not consume data | Does not consume data |
| nocxsptable | Does not consume data | Does not consume data |
| noextrasprl | Does not consume data | Does not consume data |
| nofeaturethrottle | Does not consume data | Does not consume data |
| nogrowautofit | Does not consume data | Does not consume data |
| noindnmbrts | Does not consume data | Does not consume data |
| nojkernpunct | Does not consume data | Does not consume data |
| nolead | Does not consume data | Does not consume data |
| noline | Does not consume data | Does not consume data |
| nolnhtadjtbl | Does not consume data | Does not consume data |
| nonesttables | Consumes data | Consumes data |
| nonshppict | Does not consume data | Consumes data |
| nooverflow | Does not consume data | Does not consume data |
| noproof | Does not consume data | Does not consume data |
| noqfpromote | Does not consume data | Does not consume data |
| nosectexpand | Does not consume data | Consumes data |
| nosnaplinegrid | Does not consume data | Does not consume data |
| nospaceforul | Does not consume data | Does not consume data |
| nosupersub | Does not consume data | Does not consume data |
| notabind | Does not consume data | Does not consume data |
| notbrkcnstfrctbl | Does not consume data | Does not consume data |
| notcvasp | Does not consume data | Does not consume data |
| notvatxbx | Does not consume data | Does not consume data |
| nouicompat | Does not consume data | Does not consume data |
| noultrlspc | Does not consume data | Does not consume data |
| nowidctlpar | Does not consume data | Does not consume data |
| nowrap | Does not consume data | Does not consume data |
| nowwrap | Does not consume data | Does not consume data |
| noxlattoyen | Does not consume data | Does not consume data |
| objalias | Consumes data | Consumes data |
| objattph | Does not consume data | Does not consume data |
| objautlink | Does not consume data | Does not consume data |
| objclass | Consumes data | Consumes data |
| objdata | Consumes data | Consumes data |
| object | Consumes data | Consumes data |
| objemb | Does not consume data | Does not consume data |
| objhtml | Does not consume data | Does not consume data |
| objicemb | Does not consume data | Does not consume data |
| objlink | Does not consume data | Does not consume data |
| objlock | Does not consume data | Does not consume data |
| objname | Consumes data | Consumes data |
| objocx | Does not consume data | Does not consume data |
| objpub | Does not consume data | Does not consume data |
| objsect | Consumes data | Consumes data |
| objsetsize | Does not consume data | Does not consume data |
| objsub | Consumes data | Consumes data |
| objtime | Does not consume data | Consumes data |
| objupdate | Does not consume data | Does not consume data |
| oldas | Does not consume data | Does not consume data |
| oldcprops | Consumes data | Consumes data |
| oldlinewrap | Does not consume data | Does not consume data |
| oldpprops | Consumes data | Consumes data |
| oldsprops | Consumes data | Consumes data |
| oldtprops | Consumes data | Consumes data |
| oleclsid | Consumes data | Consumes data |
| operator | Consumes data | Consumes data |
| otblrul | Does not consume data | Does not consume data |
| overlay | Does not consume data | Does not consume data |
| pagebb | Does not consume data | Does not consume data |
| panose | Consumes data | Consumes data |
| pard | Does not consume data | Does not consume data |
| password | Consumes data | Consumes data |
| passwordhash | Consumes data | Consumes data |
| pc | Does not consume data | Does not consume data |
| pca | Does not consume data | Does not consume data |
| pgbrdrb | Does not consume data | Does not consume data |
| pgbrdrfoot | Does not consume data | Does not consume data |
| pgbrdrhead | Does not consume data | Does not consume data |
| pgbrdrl | Does not consume data | Does not consume data |
| pgbrdrr | Does not consume data | Does not consume data |
| pgbrdrsnap | Does not consume data | Does not consume data |
| pgbrdrt | Does not consume data | Does not consume data |
| pgnbidia | Does not consume data | Does not consume data |
| pgnbidib | Does not consume data | Does not consume data |
| pgnchosung | Does not consume data | Does not consume data |
| pgncnum | Does not consume data | Does not consume data |
| pgncont | Does not consume data | Does not consume data |
| pgndbnum | Does not consume data | Does not consume data |
| pgndbnumd | Does not consume data | Does not consume data |
| pgndbnumk | Does not consume data | Does not consume data |
| pgndbnumt | Does not consume data | Does not consume data |
| pgndec | Does not consume data | Does not consume data |
| pgndecd | Does not consume data | Does not consume data |
| pgnganada | Does not consume data | Does not consume data |
| pgngbnum | Does not consume data | Does not consume data |
| pgngbnumd | Does not consume data | Does not consume data |
| pgngbnumk | Does not consume data | Does not consume data |
| pgngbnuml | Does not consume data | Does not consume data |
| pgnhindia | Does not consume data | Does not consume data |
| pgnhindib | Does not consume data | Does not consume data |
| pgnhindic | Does not consume data | Does not consume data |
| pgnhindid | Does not consume data | Does not consume data |
| pgnhnsc | Does not consume data | Does not consume data |
| pgnhnsh | Does not consume data | Does not consume data |
| pgnhnsm | Does not consume data | Does not consume data |
| pgnhnsn | Does not consume data | Does not consume data |
| pgnhnsp | Does not consume data | Does not consume data |
| pgnid | Does not consume data | Does not consume data |
| pgnlcltr | Does not consume data | Does not consume data |
| pgnlcrm | Does not consume data | Does not consume data |
| pgnrestart | Does not consume data | Does not consume data |
| pgnthaia | Does not consume data | Does not consume data |
| pgnthaib | Does not consume data | Does not consume data |
| pgnthaic | Does not consume data | Does not consume data |
| pgnucltr | Does not consume data | Does not consume data |
| pgnucrm | Does not consume data | Does not consume data |
| pgnvieta | Does not consume data | Does not consume data |
| pgnzodiac | Does not consume data | Does not consume data |
| pgnzodiacd | Does not consume data | Does not consume data |
| pgnzodiacl | Does not consume data | Does not consume data |
| pgp | Consumes data | Consumes data |
| pgptbl | Consumes data | Consumes data |
| phcol | Does not consume data | Does not consume data |
| phmrg | Does not consume data | Does not consume data |
| phpg | Does not consume data | Does not consume data |
| picbmp | Does not consume data | Does not consume data |
| picprop | Consumes data | Consumes data |
| picscaled | Does not consume data | Does not consume data |
| pict | Consumes data | Consumes data |
| pindtabqc | Does not consume data | Does not consume data |
| pindtabql | Does not consume data | Does not consume data |
| pindtabqr | Does not consume data | Does not consume data |
| plain | Does not consume data | Does not consume data |
| pmartabqc | Does not consume data | Does not consume data |
| pmartabql | Does not consume data | Does not consume data |
| pmartabqr | Does not consume data | Does not consume data |
| pn | Consumes data | Consumes data |
| pnacross | Does not consume data | Does not consume data |
| pnaiu | Does not consume data | Consumes data |
| pnaiud | Consumes data | Consumes data |
| pnaiueo | Does not consume data | Does not consume data |
| pnaiueod | Does not consume data | Does not consume data |
| pnbidia | Does not consume data | Does not consume data |
| pnbidib | Does not consume data | Does not consume data |
| pncard | Does not consume data | Does not consume data |
| pnchosung | Does not consume data | Does not consume data |
| pncnum | Does not consume data | Does not consume data |
| pndbnum | Does not consume data | Does not consume data |
| pndbnumd | Does not consume data | Does not consume data |
| pndbnumk | Does not consume data | Does not consume data |
| pndbnuml | Does not consume data | Does not consume data |
| pndbnumt | Does not consume data | Does not consume data |
| pndec | Does not consume data | Does not consume data |
| pndecd | Does not consume data | Does not consume data |
| pnganada | Does not consume data | Does not consume data |
| pngblip | Does not consume data | Does not consume data |
| pngbnum | Does not consume data | Does not consume data |
| pngbnumd | Does not consume data | Does not consume data |
| pngbnumk | Does not consume data | Does not consume data |
| pngbnuml | Does not consume data | Does not consume data |
| pnhang | Does not consume data | Does not consume data |
| pniroha | Does not consume data | Does not consume data |
| pnirohad | Does not consume data | Does not consume data |
| pnlcltr | Does not consume data | Does not consume data |
| pnlcrm | Does not consume data | Does not consume data |
| pnlvlblt | Does not consume data | Does not consume data |
| pnlvlbody | Does not consume data | Does not consume data |
| pnlvlcont | Does not consume data | Does not consume data |
| pnnumonce | Does not consume data | Does not consume data |
| pnord | Does not consume data | Does not consume data |
| pnordt | Does not consume data | Does not consume data |
| pnprev | Does not consume data | Does not consume data |
| pnqc | Does not consume data | Does not consume data |
| pnql | Does not consume data | Does not consume data |
| pnqr | Does not consume data | Does not consume data |
| pnrestart | Does not consume data | Does not consume data |
| pnrnot | Does not consume data | Does not consume data |
| pnseclvl | Consumes data | Consumes data |
| pntext | Consumes data | Consumes data |
| pntxta | Consumes data | Consumes data |
| pntxtb | Consumes data | Consumes data |
| pnucltr | Does not consume data | Does not consume data |
| pnucrm | Does not consume data | Does not consume data |
| pnuld | Does not consume data | Does not consume data |
| pnuldash | Does not consume data | Does not consume data |
| pnuldashd | Does not consume data | Does not consume data |
| pnuldashdd | Does not consume data | Does not consume data |
| pnuldb | Does not consume data | Does not consume data |
| pnulhair | Does not consume data | Does not consume data |
| pnulnone | Does not consume data | Does not consume data |
| pnulth | Does not consume data | Does not consume data |
| pnulw | Does not consume data | Does not consume data |
| pnulwave | Does not consume data | Does not consume data |
| pnzodiac | Does not consume data | Does not consume data |
| pnzodiacd | Does not consume data | Does not consume data |
| pnzodiacl | Does not consume data | Does not consume data |
| posxc | Does not consume data | Does not consume data |
| posxi | Does not consume data | Does not consume data |
| posxl | Does not consume data | Does not consume data |
| posxo | Does not consume data | Does not consume data |
| posxr | Does not consume data | Does not consume data |
| posyb | Does not consume data | Does not consume data |
| posyc | Does not consume data | Does not consume data |
| posyil | Does not consume data | Does not consume data |
| posyin | Does not consume data | Does not consume data |
| posyout | Does not consume data | Does not consume data |
| posyt | Does not consume data | Does not consume data |
| prcolbl | Does not consume data | Does not consume data |
| printdata | Does not consume data | Does not consume data |
| printim | Consumes data | Consumes data |
| private | Does not consume data | Does not consume data |
| propname | Consumes data | Consumes data |
| protend | Consumes data | Consumes data |
| protstart | Consumes data | Consumes data |
| protusertbl | Consumes data | Consumes data |
| psover | Does not consume data | Does not consume data |
| ptabldot | Does not consume data | Does not consume data |
| ptablmdot | Does not consume data | Does not consume data |
| ptablminus | Does not consume data | Does not consume data |
| ptablnone | Does not consume data | Does not consume data |
| ptabluscore | Does not consume data | Does not consume data |
| pubauto | Does not consume data | Consumes data |
| pvmrg | Does not consume data | Does not consume data |
| pvpara | Does not consume data | Does not consume data |
| pvpg | Does not consume data | Does not consume data |
| pxe | Does not consume data | Does not consume data |
| qc | Does not consume data | Does not consume data |
| qd | Does not consume data | Does not consume data |
| qj | Does not consume data | Does not consume data |
| ql | Does not consume data | Does not consume data |
| qr | Does not consume data | Does not consume data |
| qt | Does not consume data | Does not consume data |
| rawclbgbdiag | Does not consume data | Does not consume data |
| rawclbgcross | Does not consume data | Does not consume data |
| rawclbgdcross | Does not consume data | Does not consume data |
| rawclbgdkbdiag | Does not consume data | Does not consume data |
| rawclbgdkcross | Does not consume data | Does not consume data |
| rawclbgdkdcross | Does not consume data | Does not consume data |
| rawclbgdkfdiag | Does not consume data | Does not consume data |
| rawclbgdkhor | Does not consume data | Does not consume data |
| rawclbgdkvert | Does not consume data | Does not consume data |
| rawclbgfdiag | Does not consume data | Does not consume data |
| rawclbghoriz | Does not consume data | Does not consume data |
| rawclbgvert | Does not consume data | Does not consume data |
| readonlyrecommended | Does not consume data | Does not consume data |
| readprot | Does not consume data | Does not consume data |
| remdttm | Does not consume data | Does not consume data |
| rempersonalinfo | Does not consume data | Does not consume data |
| result | Consumes data | Consumes data |
| revisions | Does not consume data | Does not consume data |
| revprot | Does not consume data | Does not consume data |
| revtbl | Consumes data | Consumes data |
| revtim | Consumes data | Consumes data |
| rsidtbl | Does not consume data | Does not consume data |
| rsltbmp | Does not consume data | Does not consume data |
| rslthtml | Does not consume data | Does not consume data |
| rsltmerge | Does not consume data | Does not consume data |
| rsltpict | Does not consume data | Does not consume data |
| rsltrtf | Does not consume data | Does not consume data |
| rslttxt | Does not consume data | Does not consume data |
| rtf | Does not consume data | Does not consume data |
| rtlch | Does not consume data | Does not consume data |
| rtldoc | Does not consume data | Does not consume data |
| rtlgutter | Does not consume data | Does not consume data |
| rtlpar | Does not consume data | Does not consume data |
| rtlrow | Does not consume data | Does not consume data |
| rtlsect | Does not consume data | Does not consume data |
| rxe | Consumes data | Consumes data |
| saftnnalc | Does not consume data | Does not consume data |
| saftnnar | Does not consume data | Does not consume data |
| saftnnauc | Does not consume data | Does not consume data |
| saftnnchi | Does not consume data | Does not consume data |
| saftnnchosung | Does not consume data | Does not consume data |
| saftnncnum | Does not consume data | Does not consume data |
| saftnndbar | Does not consume data | Does not consume data |
| saftnndbnum | Does not consume data | Does not consume data |
| saftnndbnumd | Does not consume data | Does not consume data |
| saftnndbnumk | Does not consume data | Does not consume data |
| saftnndbnumt | Does not consume data | Does not consume data |
| saftnnganada | Does not consume data | Does not consume data |
| saftnngbnum | Does not consume data | Does not consume data |
| saftnngbnumd | Does not consume data | Does not consume data |
| saftnngbnumk | Does not consume data | Does not consume data |
| saftnngbnuml | Does not consume data | Does not consume data |
| saftnnrlc | Does not consume data | Does not consume data |
| saftnnruc | Does not consume data | Does not consume data |
| saftnnzodiac | Does not consume data | Does not consume data |
| saftnnzodiacd | Does not consume data | Does not consume data |
| saftnnzodiacl | Does not consume data | Does not consume data |
| saftnrestart | Does not consume data | Does not consume data |
| saftnrstcont | Does not consume data | Does not consume data |
| sautoupd | Does not consume data | Does not consume data |
| saveinvalidxml | Does not consume data | Does not consume data |
| saveprevpict | Consumes data | Consumes data |
| sbkcol | Does not consume data | Does not consume data |
| sbkeven | Does not consume data | Does not consume data |
| sbknone | Does not consume data | Does not consume data |
| sbkodd | Does not consume data | Does not consume data |
| sbkpage | Does not consume data | Does not consume data |
| sbys | Does not consume data | Does not consume data |
| scompose | Does not consume data | Does not consume data |
| sectd | Does not consume data | Does not consume data |
| sectdefaultcl | Does not consume data | Does not consume data |
| sectspecifycl | Does not consume data | Does not consume data |
| sectspecifygen | Does not consume data | Consumes data |
| sectspecifyl | Does not consume data | Does not consume data |
| sectunlocked | Does not consume data | Does not consume data |
| sftnbj | Does not consume data | Does not consume data |
| sftnnalc | Does not consume data | Does not consume data |
| sftnnar | Does not consume data | Does not consume data |
| sftnnauc | Does not consume data | Does not consume data |
| sftnnchi | Does not consume data | Does not consume data |
| sftnnchosung | Does not consume data | Does not consume data |
| sftnncnum | Does not consume data | Does not consume data |
| sftnndbar | Does not consume data | Does not consume data |
| sftnndbnum | Does not consume data | Does not consume data |
| sftnndbnumd | Does not consume data | Does not consume data |
| sftnndbnumk | Does not consume data | Does not consume data |
| sftnndbnumt | Does not consume data | Does not consume data |
| sftnnganada | Does not consume data | Does not consume data |
| sftnngbnum | Does not consume data | Does not consume data |
| sftnngbnumd | Does not consume data | Does not consume data |
| sftnngbnumk | Does not consume data | Does not consume data |
| sftnngbnuml | Does not consume data | Does not consume data |
| sftnnrlc | Does not consume data | Does not consume data |
| sftnnruc | Does not consume data | Does not consume data |
| sftnnzodiac | Does not consume data | Does not consume data |
| sftnnzodiacd | Does not consume data | Does not consume data |
| sftnnzodiacl | Does not consume data | Does not consume data |
| sftnrestart | Does not consume data | Does not consume data |
| sftnrstcont | Does not consume data | Does not consume data |
| sftnrstpg | Does not consume data | Does not consume data |
| sftntj | Does not consume data | Does not consume data |
| shidden | Does not consume data | Does not consume data |
| shift | Does not consume data | Does not consume data |
| shp | Consumes data | Consumes data |
| shpbxcolumn | Does not consume data | Does not consume data |
| shpbxignore | Does not consume data | Does not consume data |
| shpbxmargin | Does not consume data | Does not consume data |
| shpbxpage | Does not consume data | Does not consume data |
| shpbyignore | Does not consume data | Does not consume data |
| shpbymargin | Does not consume data | Does not consume data |
| shpbypage | Does not consume data | Does not consume data |
| shpbypara | Does not consume data | Does not consume data |
| shpgrp | Consumes data | Consumes data |
| shpinst | Consumes data | Consumes data |
| shplockanchor | Does not consume data | Does not consume data |
| shppict | Consumes data | Consumes data |
| shprslt | Consumes data | Consumes data |
| shptxt | Consumes data | Consumes data |
| slocked | Does not consume data | Does not consume data |
| sn | Consumes data | Consumes data |
| snaptogridincell | Does not consume data | Does not consume data |
| softcol | Does not consume data | Does not consume data |
| softline | Does not consume data | Does not consume data |
| softpage | Does not consume data | Does not consume data |
| sp | Consumes data | Consumes data |
| spersonal | Does not consume data | Does not consume data |
| spltpgpar | Does not consume data | Does not consume data |
| splytwnine | Does not consume data | Does not consume data |
| sprsbsp | Does not consume data | Does not consume data |
| sprslnsp | Does not consume data | Does not consume data |
| sprsspbf | Does not consume data | Does not consume data |
| sprstsm | Does not consume data | Does not consume data |
| sprstsp | Does not consume data | Does not consume data |
| spv | Does not consume data | Does not consume data |
| sqformat | Does not consume data | Does not consume data |
| sreply | Does not consume data | Does not consume data |
| staticval | Consumes data | Consumes data |
| stylelock | Does not consume data | Does not consume data |
| stylelockbackcomp | Does not consume data | Does not consume data |
| stylelockenforced | Does not consume data | Does not consume data |
| stylelockqfset | Does not consume data | Does not consume data |
| stylelocktheme | Does not consume data | Does not consume data |
| stylesheet | Consumes data | Consumes data |
| sub | Does not consume data | Does not consume data |
| subfontbysize | Does not consume data | Does not consume data |
| subject | Consumes data | Consumes data |
| super | Does not consume data | Does not consume data |
| sv | Consumes data | Consumes data |
| svb | Consumes data | Consumes data |
| swpbdr | Does not consume data | Does not consume data |
| tabsnoovrlp | Does not consume data | Does not consume data |
| taprtl | Does not consume data | Does not consume data |
| tbllkbestfit | Does not consume data | Does not consume data |
| tbllkborder | Does not consume data | Does not consume data |
| tbllkcolor | Does not consume data | Does not consume data |
| tbllkfont | Does not consume data | Does not consume data |
| tbllkhdrcols | Does not consume data | Does not consume data |
| tbllkhdrrows | Does not consume data | Does not consume data |
| tbllklastcol | Does not consume data | Does not consume data |
| tbllklastrow | Does not consume data | Does not consume data |
| tbllknocolband | Does not consume data | Does not consume data |
| tbllknorowband | Does not consume data | Does not consume data |
| tbllkshading | Does not consume data | Does not consume data |
| tc | Consumes data | Consumes data |
| tcelld | Does not consume data | Does not consume data |
| tcn | Does not consume data | Does not consume data |
| template | Consumes data | Consumes data |
| themedata | Consumes data | Consumes data |
| time | Does not consume data | Does not consume data |
| title | Consumes data | Consumes data |
| titlepg | Does not consume data | Does not consume data |
| tldot | Does not consume data | Does not consume data |
| tleq | Does not consume data | Consumes data |
| tlhyph | Does not consume data | Does not consume data |
| tlmdot | Does not consume data | Does not consume data |
| tlth | Does not consume data | Does not consume data |
| tlul | Does not consume data | Does not consume data |
| toplinepunct | Does not consume data | Does not consume data |
| tphcol | Does not consume data | Does not consume data |
| tphmrg | Does not consume data | Does not consume data |
| tphpg | Does not consume data | Does not consume data |
| tposxc | Does not consume data | Does not consume data |
| tposxi | Does not consume data | Does not consume data |
| tposxl | Does not consume data | Does not consume data |
| tposxo | Does not consume data | Does not consume data |
| tposxr | Does not consume data | Does not consume data |
| tposyb | Does not consume data | Does not consume data |
| tposyc | Does not consume data | Does not consume data |
| tposyil | Does not consume data | Does not consume data |
| tposyin | Does not consume data | Does not consume data |
| tposyout | Does not consume data | Does not consume data |
| tposyt | Does not consume data | Does not consume data |
| tpvmrg | Does not consume data | Does not consume data |
| tpvpara | Does not consume data | Does not consume data |
| tpvpg | Does not consume data | Does not consume data |
| tqc | Does not consume data | Does not consume data |
| tqdec | Does not consume data | Does not consume data |
| tqr | Does not consume data | Does not consume data |
| transmf | Does not consume data | Does not consume data |
| trbgbdiag | Does not consume data | Does not consume data |
| trbgcross | Does not consume data | Does not consume data |
| trbgdcross | Does not consume data | Does not consume data |
| trbgdkbdiag | Does not consume data | Does not consume data |
| trbgdkcross | Does not consume data | Does not consume data |
| trbgdkdcross | Does not consume data | Does not consume data |
| trbgdkfdiag | Does not consume data | Does not consume data |
| trbgdkhor | Does not consume data | Does not consume data |
| trbgdkvert | Does not consume data | Does not consume data |
| trbgfdiag | Does not consume data | Does not consume data |
| trbghoriz | Does not consume data | Does not consume data |
| trbgvert | Does not consume data | Does not consume data |
| trbrdrb | Does not consume data | Does not consume data |
| trbrdrh | Does not consume data | Does not consume data |
| trbrdrl | Does not consume data | Does not consume data |
| trbrdrr | Does not consume data | Does not consume data |
| trbrdrt | Does not consume data | Does not consume data |
| trbrdrv | Does not consume data | Does not consume data |
| trhdr | Does not consume data | Does not consume data |
| trkeep | Does not consume data | Does not consume data |
| trkeepfollow | Does not consume data | Does not consume data |
| trowd | Does not consume data | Does not consume data |
| trqc | Does not consume data | Does not consume data |
| trql | Does not consume data | Does not consume data |
| trqr | Does not consume data | Does not consume data |
| truncatefontheight | Does not consume data | Does not consume data |
| truncex | Does not consume data | Does not consume data |
| tsbgbdiag | Does not consume data | Does not consume data |
| tsbgcross | Does not consume data | Does not consume data |
| tsbgdcross | Does not consume data | Does not consume data |
| tsbgdkbdiag | Does not consume data | Does not consume data |
| tsbgdkcross | Does not consume data | Does not consume data |
| tsbgdkdcross | Does not consume data | Does not consume data |
| tsbgdkfdiag | Does not consume data | Does not consume data |
| tsbgdkhor | Does not consume data | Does not consume data |
| tsbgdkvert | Does not consume data | Does not consume data |
| tsbgfdiag | Does not consume data | Does not consume data |
| tsbghoriz | Does not consume data | Does not consume data |
| tsbgvert | Does not consume data | Does not consume data |
| tsbrdrb | Does not consume data | Does not consume data |
| tsbrdrdgl | Does not consume data | Does not consume data |
| tsbrdrdgr | Does not consume data | Does not consume data |
| tsbrdrh | Does not consume data | Does not consume data |
| tsbrdrl | Does not consume data | Does not consume data |
| tsbrdrr | Does not consume data | Does not consume data |
| tsbrdrr | Does not consume data | Does not consume data |
| tsbrdrt | Does not consume data | Does not consume data |
| tsbrdrv | Does not consume data | Does not consume data |
| tscbandhorzeven | Does not consume data | Does not consume data |
| tscbandhorzodd | Does not consume data | Does not consume data |
| tscbandverteven | Does not consume data | Does not consume data |
| tscbandvertodd | Does not consume data | Does not consume data |
| tscfirstcol | Does not consume data | Does not consume data |
| tscfirstrow | Does not consume data | Does not consume data |
| tsclastcol | Does not consume data | Does not consume data |
| tsclastrow | Does not consume data | Does not consume data |
| tscnecell | Does not consume data | Does not consume data |
| tscnwcell | Does not consume data | Does not consume data |
| tscsecell | Does not consume data | Does not consume data |
| tscswcell | Does not consume data | Does not consume data |
| tsd | Does not consume data | Does not consume data |
| tsnowrap | Does not consume data | Does not consume data |
| tsrowd | Does not consume data | Does not consume data |
| tsvertalb | Does not consume data | Does not consume data |
| tsvertalc | Does not consume data | Does not consume data |
| tsvertalt | Does not consume data | Does not consume data |
| twoonone | Does not consume data | Does not consume data |
| txbxtwalways | Does not consume data | Does not consume data |
| txbxtwfirst | Does not consume data | Does not consume data |
| txbxtwfirstlast | Does not consume data | Does not consume data |
| txbxtwlast | Does not consume data | Does not consume data |
| txbxtwno | Does not consume data | Does not consume data |
| txe | Consumes data | Consumes data |
| ud | Consumes data | Consumes data |
| uld | Does not consume data | Does not consume data |
| ulnone | Does not consume data | Does not consume data |
| ulw | Does not consume data | Does not consume data |
| upr | Consumes data | Consumes data |
| useltbaln | Does not consume data | Does not consume data |
| usenormstyforlist | Does not consume data | Does not consume data |
| userprops | Consumes data | Consumes data |
| usexform | Does not consume data | Does not consume data |
| utinl | Does not consume data | Does not consume data |
| vertal | Does not consume data | Does not consume data |
| vertalb | Does not consume data | Consumes data |
| vertalc | Does not consume data | Does not consume data |
| vertalj | Does not consume data | Does not consume data |
| vertalt | Does not consume data | Does not consume data |
| vertdoc | Does not consume data | Does not consume data |
| vertsect | Does not consume data | Does not consume data |
| viewnobound | Does not consume data | Does not consume data |
| webhidden | Does not consume data | Does not consume data |
| wgrffmtfilter | Consumes data | Consumes data |
| widctlpar | Does not consume data | Does not consume data |
| widowctrl | Does not consume data | Does not consume data |
| windowcaption | Consumes data | Consumes data |
| wpeqn | Does not consume data | Does not consume data |
| wpjst | Does not consume data | Does not consume data |
| wpsp | Does not consume data | Does not consume data |
| wraparound | Does not consume data | Does not consume data |
| wrapdefault | Does not consume data | Does not consume data |
| wrapthrough | Does not consume data | Does not consume data |
| wraptight | Does not consume data | Does not consume data |
| wraptrsp | Does not consume data | Does not consume data |
| writereservation | Consumes data | Consumes data |
| writereservhash | Consumes data | Consumes data |
| wrppunct | Does not consume data | Does not consume data |
| xe | Consumes data | Consumes data |
| xform | Consumes data | Consumes data |
| xmlattr | Consumes data | Consumes data |
| xmlattrname | Consumes data | Consumes data |
| xmlattrvalue | Consumes data | Consumes data |
| xmlclose | Consumes data | Consumes data |
| xmlname | Consumes data | Consumes data |
| xmlnstbl | Consumes data | Consumes data |
| xmlopen | Consumes data | Consumes data |
| xmlsdttcell | Does not consume data | Does not consume data |
| xmlsdttpara | Does not consume data | Does not consume data |
| xmlsdttregular | Does not consume data | Does not consume data |
| xmlsdttrow | Does not consume data | Does not consume data |
| xmlsdttunknown | Does not consume data | Does not consume data |
| yxe | Does not consume data | Does not consume data |